WordPress hacked with sophisticated hack
There is a new WordPress hack that hackers are using to compromise your sites for email spam and for hosting pages to download malicious files.
A few points to check to see if you have been hacked using this new method:
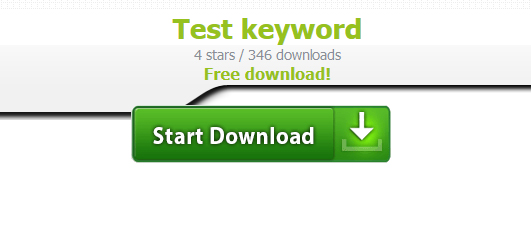
1. Check your website footer for a hyperlinked full stop, like this > . – this is often a hyperlink to your root domain with a sample query string such as “domain.com/?awert=test-keyword”. When you visit this page you will see a custom hosted-webpage with a button to a download link – often for malware.
To remove this simply edit your theme footer file and remove the basic a href code.
2. Check your index.php file in the root of your domain for compromised code. The new hack duplicates your website style to look exactly the same as your website, but with malicious includes and links to scripts. You will notice the difference straight away if your index.php file has been compromised as it is nothing like the default wordpress index.php.
To resolve this simply overwrite the compromised index.php file with a default file from an existing WordPress installation.
3. Check your wp-config.php file for a very sneaky line of code (usually at the bottom of the file). This code is something along the lines of:
“require_once (ABSPATH. ‘wp-content/plugins/ xcalendar/xcalendar.php ‘);”
This line of code runs a plugin that has been installed to your WordPress site without you knowing.
4. Login to your WordPress admin panel and go to the plugins section. You will see a new plugin present in the list called “Seo Advisor” by “Phil Smitter” with a link to the plugin author page seoadvisor.com to try and make it look genuine. Delete this plugin and remove all files from your server. This runs the xcalendar files.
5. If you have any of the steps above then it is probably also worth checking your users in the WordPress admin panel. Often when a site becomes compromised in this way new additional admin accounts are created with admin permissions. Usernames such as this usually include; administrator, root, admin93, admin47, admin21 etc.
Delete these admin accounts.
Once you have taken the above steps it is time to lock your site down and try to locate any other malicious files that may be hidden away in your folders. Common hiding places are the uploads folder and wp-includes folder.
Once you have done this the following plugins are worth installing to help you monitor and protect your WordPress site from future hacks and allows you to respond quickly:
- iThemes Security
- WordFence
- BruteProtect
- Captcha by BestWebSoft
I am not affiliated with the above plugins nor do i provide support for them.